The COVID-19 crisis has pushed a digital transformation in record time. Traditional work dynamics are gone, and many of us see now our homes as where we work.
We have never been more dependent on our employer’s IT solutions. While some tackle the transition to remote work without disruptions, others experience frustration with outdated devices and unstable services. This frustration gets compounded by dealing with non-technical issues such as suboptimal ergonomics or demanding children.
Most people are used to a seamless user experience in their private lives. Despite a global explosion in service demand around the Internet, they continue to have video calls on FaceTime, share photos on Instagram, and watch movies on Netflix, exactly like before.
Employees expect comparable user experiences in their working lives. If it is poor, some may use private devices and services as alternative IT solutions. This workaround is known as “shadow IT” and it can compromise the organization’s compliance and security. The consequences from shadow IT can quickly become expensive.
A sustainable IT architecture is crucial for realizing an effective digital workplace. It must balance scalability, security, and user experience. Here is how you, as CIO, can move forward to provide a digital workplace to your employees:
1. Migrate from on-premises to the cloud
Your organization probably still relies on on-premises infrastructure to operate business services, as well as end-user services such as connectivity, communication, and collaboration.
One of the issues with on-premises infrastructure is that you have to purchase and install servers, storage, networking, and other computing resources to expand its capacity—a process that may take months in normal circumstances, let alone during a pandemic.
When the actual demand surpasses the available capacity, you have got a problem. The typical consequence is that you lose customers. In this scenario, you lose employees too, as they are unable to work.
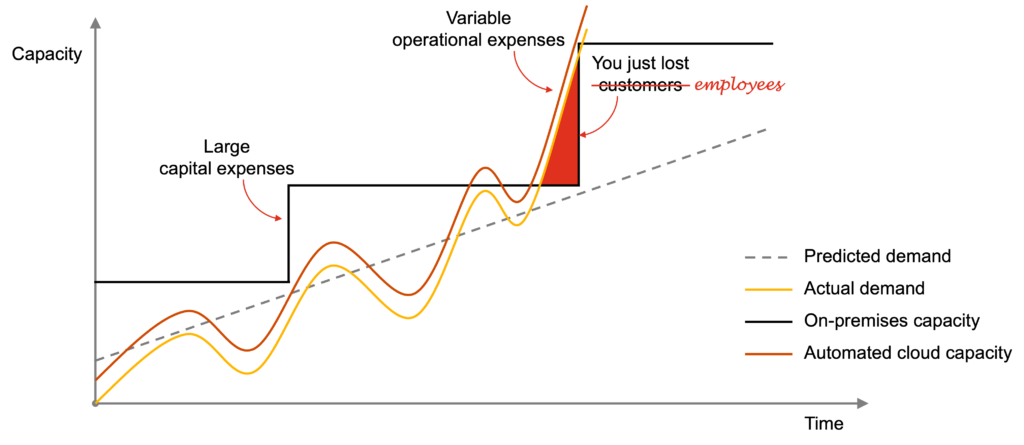
Adopt hyper-scale infrastructure and software-as-a-service
The cloud offers hyper-scale infrastructure, which allows you to rapidly provision computing resources with minimal management effort.
When exploiting automation, the available capacity can automatically scale up and down based on the actual demand. In this case, you can cope with unexpected spikes with minimal downsides, such as losing employees on the way.
Microsoft with Microsoft 365 and Google with G Suite offer cloud-based collaboration platforms. Other software-as-a-service providers cover plenty of additional capabilities for a digital workplace. You may want to widen their adoption in your organization.
2. Switch from perimeter- to zero trust security
Your organization needs to protect business and end-user services through an adequate security model.
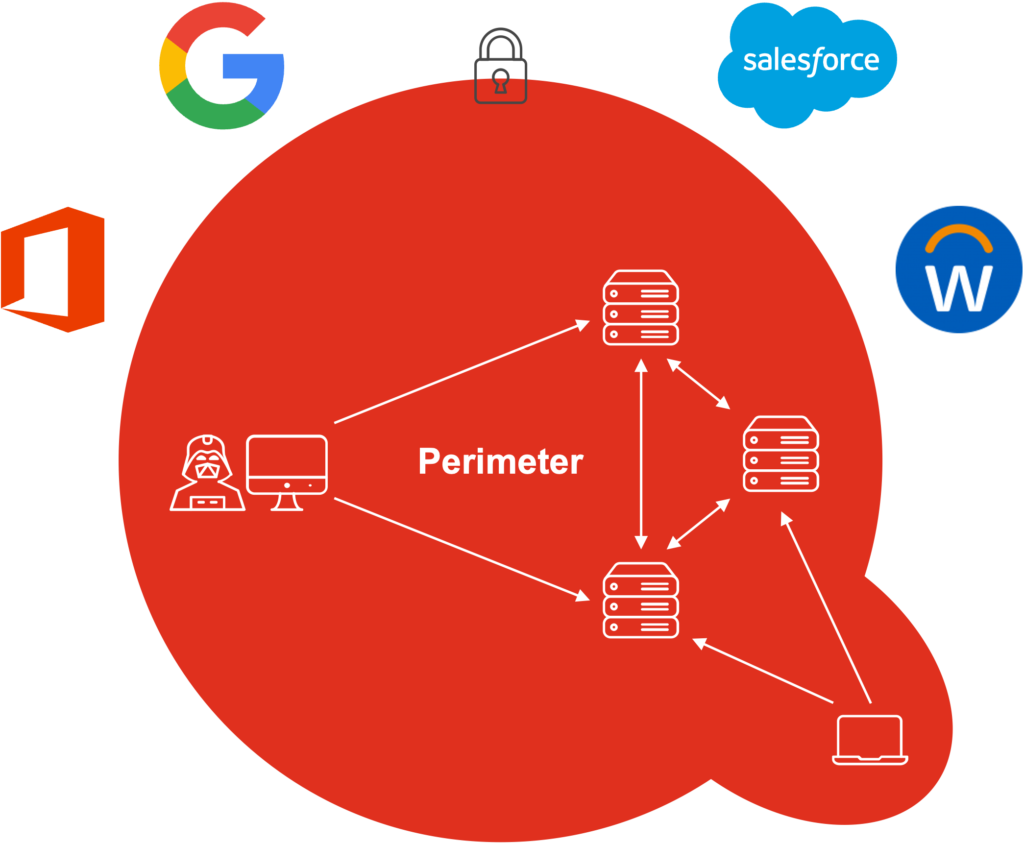
Not unlike a medieval castle, the perimeter security model relies on a secured boundary between the private side of a network, often the intranet, and the public side of a network, often the Internet.
Virtual private network (VPN), firewall, and other tools protected your IT environment from cyber threats relatively well during the ‘90s and 2000s, when you had few entry points for users and devices. However, these tools were not designed for your current IT environment, where you have heterogeneous users and devices, both on-premises and in the cloud.
Authenticate, authorize, and verify all users and devices
The zero trust security model relies on the principle that you should not trust anyone, neither inside nor outside your perimeter. You should instead authenticate, authorize, and verify all users and devices attempting to access your systems.
Identity and access management (IAM), multi-factor authentication (MFA), unified endpoint management (UEM), encryption, and other tools are better suited for this purpose. These tools allow you to flexibly combine legacy systems on-premises and modern systems in the cloud with heterogeneous users and devices.
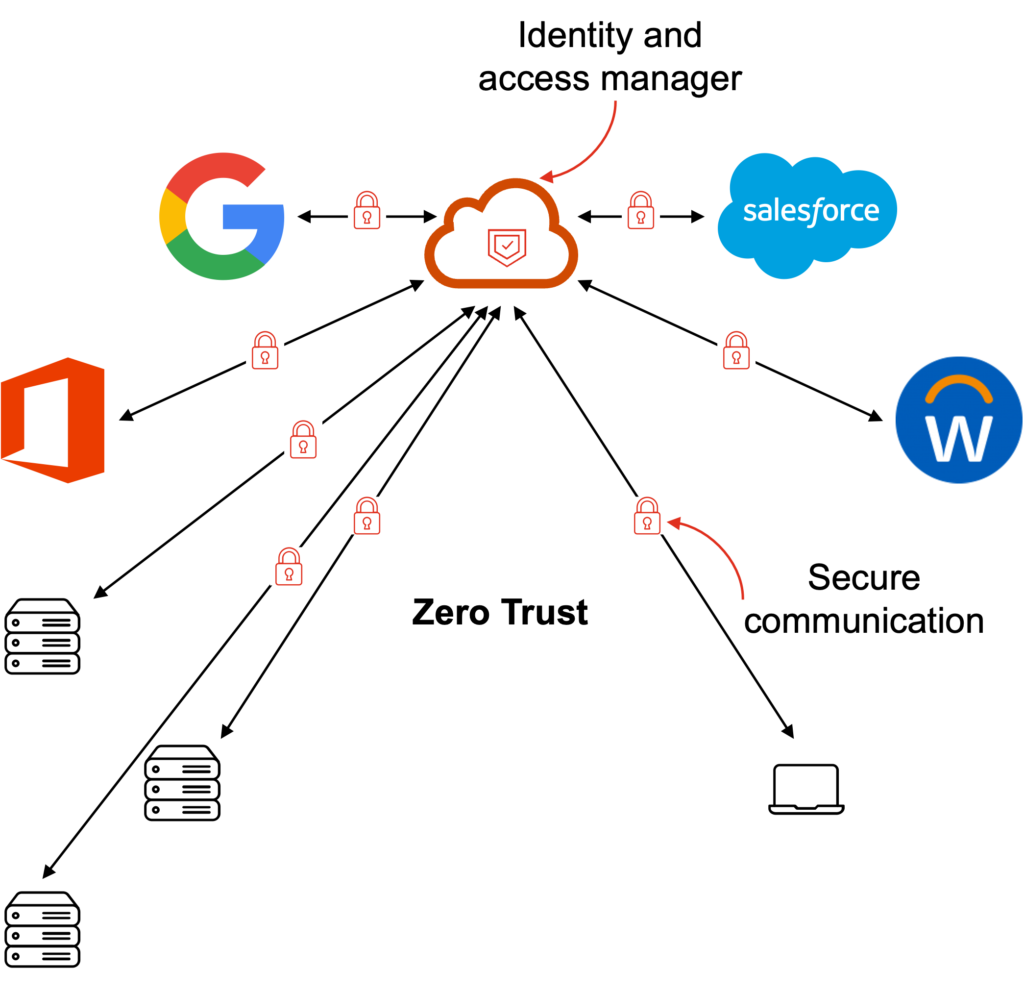
Microsoft, Google, and other major IT players recommend the zero trust security model. They adopt it in their own companies. You may want to accelerate its implementation in your organization.
3. Focus on the user experience
Your organization may have neglected the user experience of IT services. IT departments may offer employees a one-size-fits-all PC, while alternatives such as Macs and iPads may be non-supported options. Some business applications may have cumbersome user interfaces. Others may require employees to access outdated remote desktop solutions. Some communication and collaboration applications may provide redundant functionalities, which can leave employees unsure about when to use what.
Avoid shadow IT
If this goes too far, employees could feel like the IT department provided them with tools that diminish rather than enhance their productivity. Their frustration could even lead them to shadow IT, with potentially severe consequences.
There are more efficient ways of working, which can raise employee engagement. To succeed, you need to provide a quality of service comparable to the ones of Apple and Google, whose devices and services “just work.” In other words, you need to provide state-of-the-art hardware, software, and underlying IT architecture.
A digital workplace requires a comprehensive approach to delivering a consumer-oriented IT environment, where the technology is continuously improved, and the workforce is frequently upskilled.
This approach is ambitious, and is going to cost—but it may be the most forward-looking investment you can make.
A shorter version of this article was published in Norwegian in Teknisk Ukeblad on May 2020.
Leave a Reply